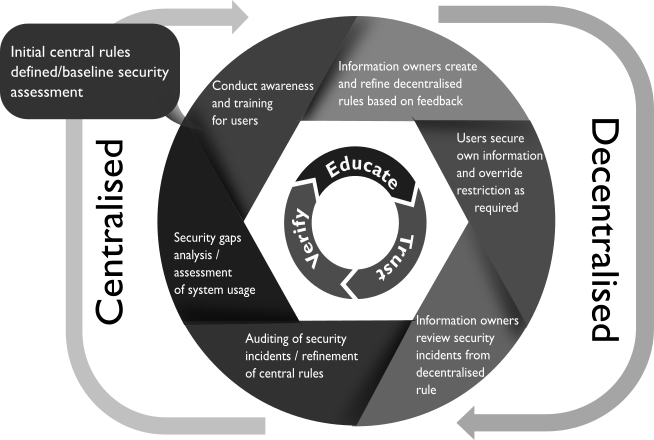
Trust but Verify People Centric Security

Integrated Discovery and Classification of Data
Empowers information owners, by providing tools, to define rules for discovery and classification of data at rest
within local and shared drives, file servers and databases. The rules and policies are applied centrally to ensure
that protection levels are set correctly and well defined sensitive data is secured.
Monitoring of Data in Motion & Data in Use

Preventing Data from being Leaked
Based on policy, prevents data movement around and out of an organisation via online and offline channels
such as on email, web, shadow sites, social media, chat, cloud, USB drives, SD Cards, printers and mobile phones.