We Have Spent Millions On Security But Still Face Leaks To The Public And The Press?
“Google accidentally leaked hundreds of thousands of customers’ personal details — and didn’t notice for 2 years”
“David Bowie, Diane Von Fürstenberg, Diego Forlán, and other famous names that appeared in HSBC’s Swiss bank leak”
NSA leaks by Edward Snowden
Secret military and diplomatic files leaked to Wikileaks by Bradly Manning
Why existing security systems like DLPs fail
1. Information Owners (Heads of Department) are unable to directly control the information for which they are responsible
Sensitive information is created daily in a decentralised manner at the departmental level. The only people who can actually decide the appropriate use of this information are the department staff themselves. Unfortunately, traditional security approaches rely on central tagging and monitoring of sensitive information and there is no automated way of tagging new information being created on a daily basis. Furthermore, as they rely on central monitors rather than departmental-level monitors, they have no idea what qualifies as inappropriate usage of sensitive information. As such, sensitive information which can actually hurt the organisation never gets tagged and monitored.
2. Existing security solutions only catch illegitimate access
3. Real sensitive information is not shared with, or monitored by, IT staff
4. IT staff cannot identify actual leakage of sensitive information
5. No education or involvement of users and so no modification of user behaviour
THE SOLUTION : CORPORATE INTEGRITY MANAGEMENT SYSTEM A SMART DLP
e-Safe Compliance is the only system to protect against both insider and outsider threats:
1. Behavioural analytics to detect potential threat points
2. Securing information at its source and eliminating the need to block
3. Empowering end-users to classify and monitor sensitive information themselves
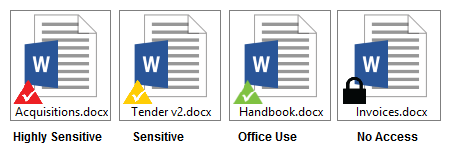
- Using e-safe Compliance information tagging utility, authorised information owners can classify large amounts of information into rules which are applied within their department.
- Information owners can classify sensitive documents as secret, confidential or internal use using document rights management. They can also specify who can access this information by defining document rights without involving the central admin.
- Potential data leak incidents which are produced by these decentralized definitions are reviewed by the information owners themselves, and, in some cases, completely without involving the IT admin. As the information owners have a good understanding of the people using the information, the operational circumstances, and what constitutes misuse of the information, they are able to identify serious misuse of information accurately.
The decentralised security facilities ensure that end-users are engaged in the maintaining the security of the information, as they can clearly see results of any mishandling, making security part of everyday operations.
4. Real-time forensic monitoring
5. Integrity management workflow
A high level diagram of the checks and balances within e-Safe Compliance is shown in figure 1 below.
 Figure 1 – Decentralized Information Monitoring System (Security is everyone’s responsibility)
Figure 1 – Decentralized Information Monitoring System (Security is everyone’s responsibility)
6. Visual signals ensure ongoing education and ensure compliance
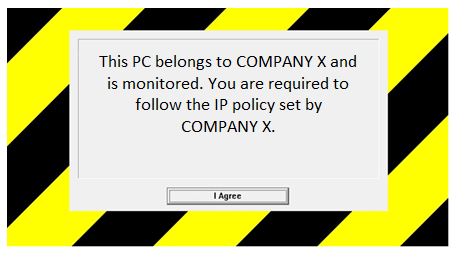
In addition to this, users are warned of any misuse of the company property through the display of a clear policy screen when logging into a company PC. This policy screen (displayed below) sends a clear, customisable message to members of staff that this machine is monitored and acts as a perfect deterrent to prevent infringement of the company’s IT policy.