Securing Documents at the Source using Universal Encryption
Universal encryption is specifically designed to address the insider threat; to achieve this requires 3 very important characteristics:
- Persistent. The encryption follows the data; it is not dependent on the device. It is never available in an unencrypted form. If either deliberate or accidental transmission to an unauthorised third party takes place it remains secure.
- Transparent. The user does not have to get involved in the public/private key verification. As most end users of the most sensitive documents are seldom IT savvy this makes it easy to use.
- Available on and off line. While access rules may be synchronised with AD it is not necessary for the device to be on-line for these rules to be applied to the document, allowing people to work while travelling and not exposing anything to insecure hotel or airline networks.
An option is also available which ensures all documents created on a specific PC or in a specific department are encrypted automatically, thus securing all information irrespective of its sensitivity level.
Document Sensitivity Levels and Usage Controls
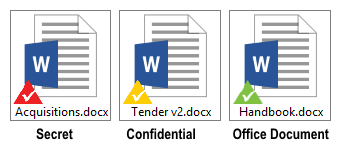
Sensitive information is normally categorised based on sensitivity levels (secret, confidential etc) which define how the information should be dealt with. Assigning sensitivity levels to information is absolutely vital for maintaining security.
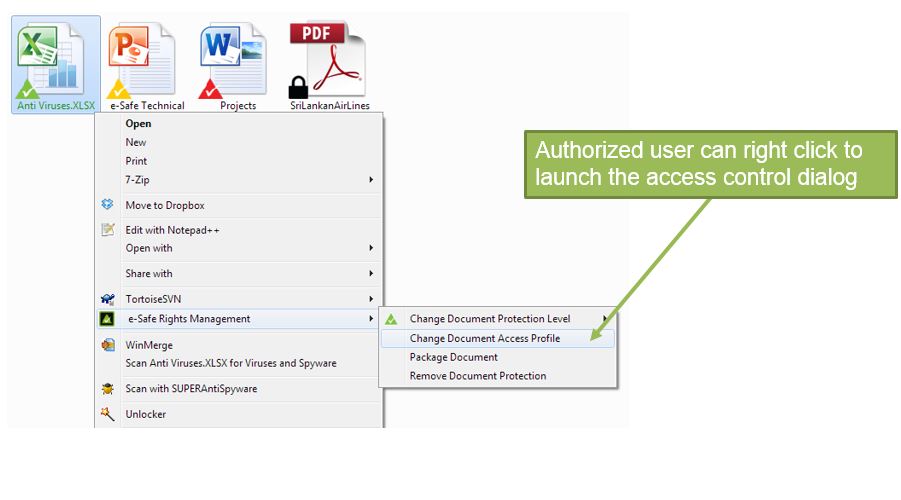
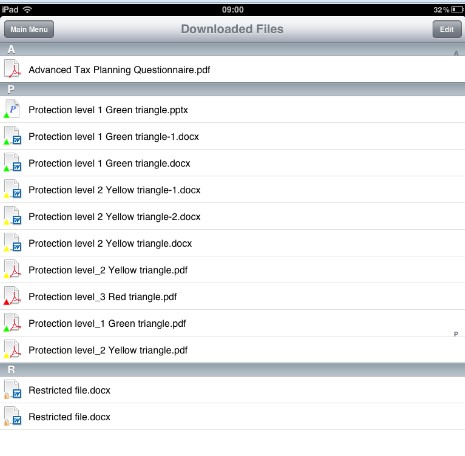
e-Safe Compliance automates this process by providing information owners with the ability to assign the correct document sensitivity level using mouse right-click options. Documents can be categorised into three levels, which are depicted by their triangle overlay icon colour.
The categorisation process automatically encrypts the document using universal encryption. Furthermore, each sensitivity level is associated with the appropriate document usage control. For example, documents at the red level are restricted from being printed or having their contents being cut/copied outside of the document.
The categorisation process automatically encrypts the document using universal encryption. Furthermore, each sensitivity level is associated with the appropriate document usage control. For example, documents at the red level are restricted from being printed or having their contents being cut/copied outside of the document.
Document Rights Management
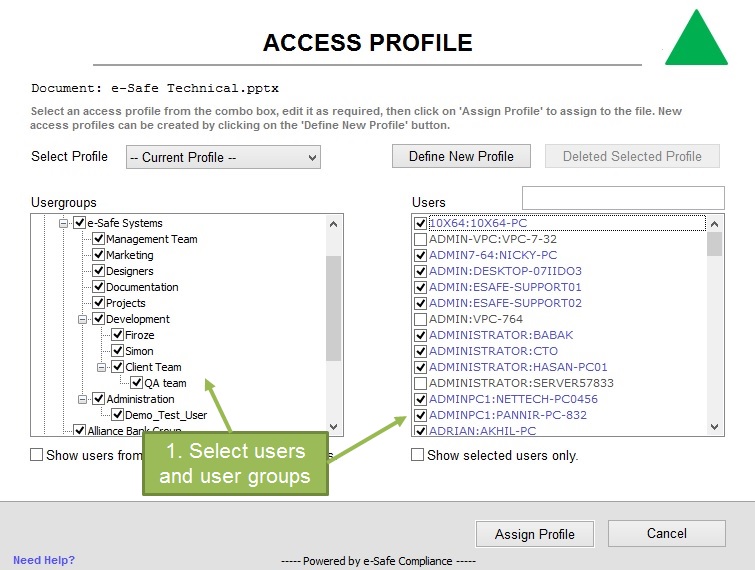
The insider threat cannot be eliminated unless access to sensitive information is limited. This is achieved by document rights management. This module allows information owners to define who can have access to a document by using mouse right-click options.
The module automatically connects to Active Directory, if available, to extract the relevant group/user information. However, the module can work without the availability of Active Directory or even when offline.
Users who do not have access to the document will see it as being locked.
Users who do not have access to the document will see it as being locked.
Overriding Document Usage Restrictions
Restricting document usage prevents users from doing their job, while just monitoring document usage results in the reviewing of a large number of incidents. e-Safe Compliance introduces a way – “allow users to remove restrictions but require them to provide a reason for doing so.”
Allowing authorised users to override restrictions by giving a reason means those users are no longer prevented from doing their job. Furthermore, the fact that they have to give a reason ensures users are aware of the importance of the information and that they will be held accountable for any misuse. This automatically ensures security of the information.
Data Protection on Mobile/BYOD Devices
In order for users to access documents encrypted using universal encryption on their smart devices, they will need to install the e-Safe iOS or Android app. The app allows users to access encrypted documents in iOS and Android devices.
All the relevant access, sensitivity levels, usage control and usage overriding-with-reason options apply to the documents which are accessed through this app. Furthermore, the complete usage of this app, and the documents accessed therein, are reported back to the server. The app can be disabled in the event that the device is lost, thereby securing the documents that are present inside the device.
Track Sensitive/Protected Documents
In order for users to access documents encrypted using universal encryption on their smart devices, they will need to install the e-Safe iOS or Android app. The app allows users to access encrypted documents in iOS and Android devices.
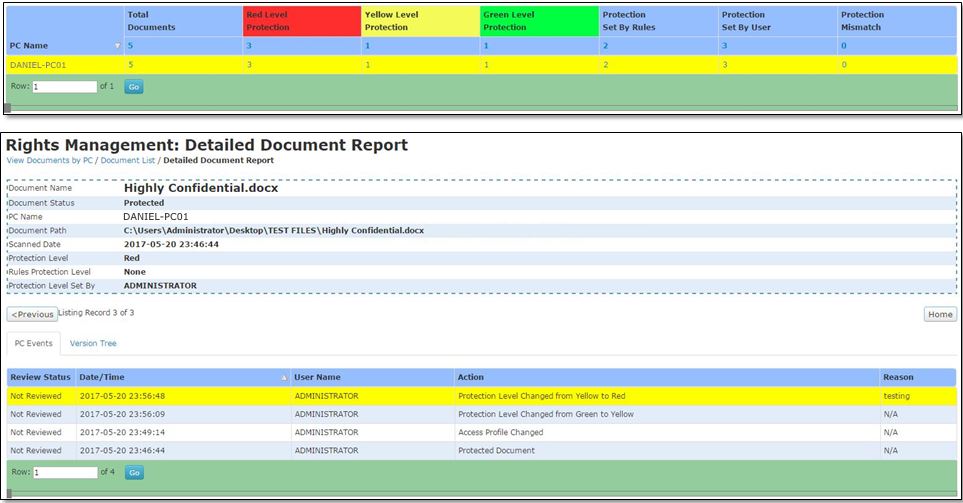
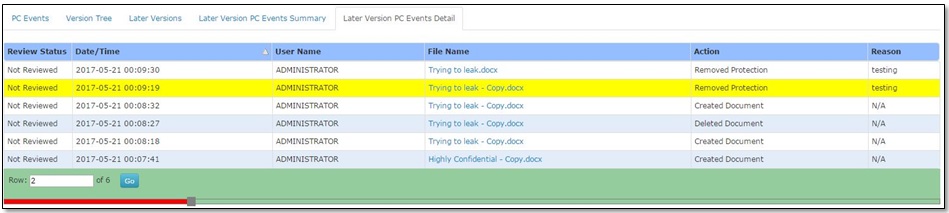
Protected documents are tracked throughout their lifecycle from creation to deletion. Reports are generated, information owners can access the reports and can also verify the users for their activities related to these documents.